My first bug bounty
September 20, 2023
I was playing FiveM (the modded version of GTA V that allows users to create their own servers and scripts) and found out that the server I was playing on had an ingame phone. Now on this phone there was a twitter application, which allowed users to post tweets with images. I knew from previous experience that FiveM uses chromium to render their UI and conveniently had devtools available.
The exploit
It was actually quite simple. While the server did filter “malicious” URLS the filtering logic wasn’t quite so good. It looked something like this:
-- Check if the URL starts with discord's media server,
-- as we know this is safe.
if not url.startsWith("https://media.discordapp.com") then
return false -- The URL is malicious!
endAt first glance this might look as pretty secure, but there’s a catch. The filtering logic didn’t account for an old URL feature: user information.
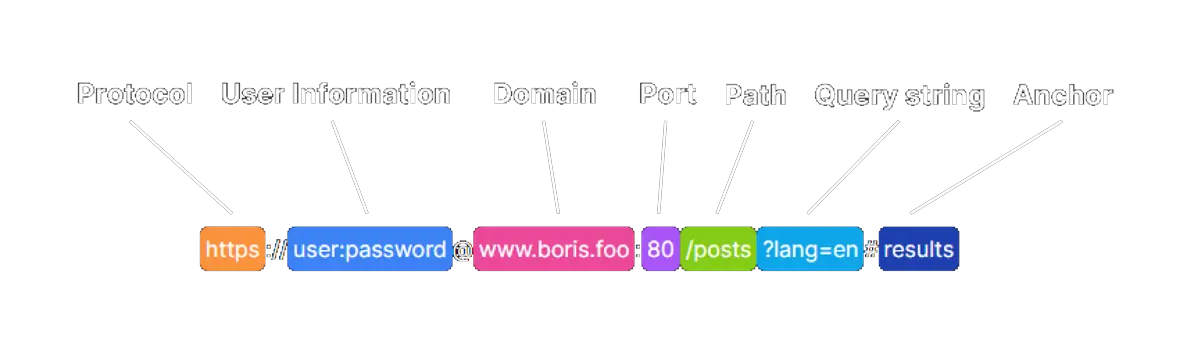
So this, for example, would bypass the malicious url check:
https://media.discordapp.com@attacker.comNow if the attacker logs all requests they can gain info about the players on the server, which is obviously quite bad. I also discovered the same issue in a messaging app on the phone, which is even worse because it allows attackers to target individual users.
After reporting this exploit to the server developers, they awarded me €100 as a bug bounty!
Bug Hunting Beyond
I looked around some popular phone applications on GitHub for FiveM and found that some had the same vulnerability. I opened some pull requests like this one.
In conclusion: Report those bugs, guys!
Copyright © 2016-2026 boris.foo, All rights reserved.